New IPS to Boost Security, Reliability and Performance of the Campus Network
Virus, Worm or Trojan is no longer a technical jargon. They are so common and their impacts are so severe that they have appeared many times in the headlines of newspaper and media, such as CNN at http://www.cnn.com/2005/TECH/internet/08/16/computer.worm/index.html.
Although anti-virus vendors are trying their best to stop these attacks, new types of virus/worm are discovered everyday. New techniques must be employed to supplement our existing methods to detect and stop these attacks.
In order to protect against the massive and evolving networking virus/worm attacks, the Computing Services Centre (CSC) had recently deployed the network based Intrusion Protection System (NIPS). In this article, we shall discuss the features of the new IPS . For background information of IPS and security appliance deployment on our campus, please read the articles on Network Computing, Issue 41 - September 2004 and Issue 47 March 2006.
Features of the new IPS
In the following sections, we will look at how our new IPS can provide unique countermeasures to stop the propagation of viruses/worms.
-
Intelligent Port Scanning detection
-
Behavior-based Denial of Service (DoS) protection (Zero Day Attack Protection)
-
Brute Force Protection for Central Servers and Application Servers
-
Multiple Segments Support - Virtual IPS
-
Programmable API for Dynamic Policy management
a. Intelligent Port Scanning detection
CityU has a large and contiguous IP address pool (more than 60,000 IP addresses). From the hacker's point of view, it is a good place to search for vulnerable hosts by performing massive port scan activities.
Although our existing IPS can perform port scanning detection and blocking functionality, after further analysis, we can still detect the following types of port scanning activities.
-
Horizontal Port Scanning
-
Scanning for the same port for the whole subnet range
-
-
Slow and Very Slow Port Scanning
-
Scanning a few hosts (5 to 10 hosts) in every 5 minutes for the whole day
-
A complete Class B network can be scanned within 2 weeks
-
Our IPS's Solution to Port Scanning
Our IPS can protect CityU from the above attacks by providing advanced and fine tunable port scanning detection and blocking functionalities:
-
Vertical Port Scanning ( scanning multiple ports on a single host)
-
Horizontal Port Scanning ( scanning single port for each host in the whole subnet)
-
ICMP (ping) scanning
-
Very slow scan
-
Scanning from many source ports
-
Scanning of multiple destination IP and ports
The most impressive feature is the "Very Slow Scan" detection which can
-
Detect and block the slow port scanning activities that only scan for 10 hosts in every 5 minutes
-
The blocking period/time will be extended based on the number of occurrences of attacks from the same source.
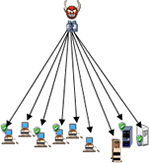
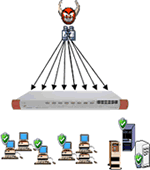
With the new IPS deployed, both the "Very fast scan" and "Very slow scan" activities are detected and blocked effectively. This further tightens the security level of our Internet gateway. The diagram below shows details of a port scanning attack and how it can be blocked by the IPS.
|

|
|
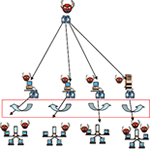
| Step 1. Hacker performs Port Scanning techniques to find targets with vulnerabilities | Step 2. Hacker can inject virus, trojan to targets with vulnerabilities found | Step 3. The infected machines further SCAN and INFECT for vulnerable hosts within INTERNAL network |
|
|
|
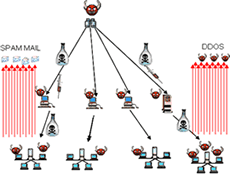
| Step 4. The hacker can issue commands to hosts with virus/trojan installed to perform further attacks. e.g. Sending of SPAM MAIL or DDOS attacks | IPS Protection: Our IPS stops the Port Scanning activities at the First Step. Thus, it prevents further infection/attack. | |
b. Behavior-based DoS and Zero Day Attack Protection
Most IPS provides signature-based attack detection mechanism. Under this approach, the attack is detected by comparing the virus/worm characteristics (file or binary footprints) with the IPS signatures database. In order to improve the accuracy, other factors such as the network ports, traffic direction, protocol handshaking information are put together to conclude a network attack.
However, as many new variants of virus/worm and vulnerabilities emerge everyday, this signature-based detection can no longer discover new attacks during the first day of their outbreak (Zero Day).
Our IPS's Solution to Zero Day DoS Attack Protection
Our IPS provides Zero Day DoS Attack Protection by a Self-Learning Adaptive System. For simplicity, the system composes of 3 self-learning and adaptive components:
-
Detection Module
-
Attack Footprints Lookup Module
-
Blocking Module
The block diagram below shows the components of the Behavior DoS protection system.
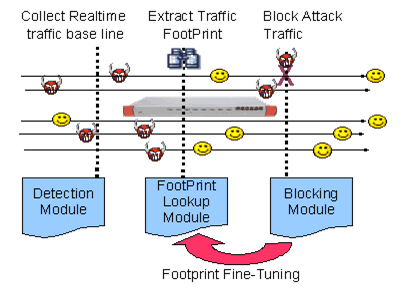
i. Detection Module
The Detection Module discovers attacks by analyzing every individual packet in real time and comparing the real time traffic parameters with the base-lined value. The traffic parameters include
-
Rate-based behavior parameters such as packet rate, traffic volume, traffic sessions, etc
-
Rate-invariant behavior parameters, such as input/output session ratio, TCP flag distribution
Rate-invariant parameters are used to reduce the false positive when there is a shape change in the traffic parameters. For example, during course registration period, the followings will be detected:
-
Shape increase in Web traffic volume (http – TCP 80 port)
-
Ratio of SYN and SYN-ACK will remain nearly constant (it is a normal Web traffic)
As the ratio of SYN and SYN-ACK remains the same for the Web traffic, the shape increase in traffic volume will NOT be classified as an attack.
Conversely, during a SYN flooding attack using Port 80, the ratio of SYN and ACK-SYN will be much higher than a normal Web traffic. The detection engine will then report an attack.
ii. Attack Footprints Lookup Module
The "attack footprints lookup" module will then try to find the pattern/characteristics of the attack traffic. This is achieved by analyzing about 17 parameters that can be found in every packet. These parameters include the packet checksum, packet size, TTL, ports, sequences no, etc. Based on these parameters, the "attack footprints lookup" module creates a highly accurate, real-time signature of this specific attack.
iii. Blocking Module
The blocking module will make use of the footprint found in the above module to block the DoS attack. Being a self-learning adaptive protection system, this module will collect the result of the blocking and feed back to the "footprint lookup" module. This process will fine-tune the effectiveness of the attack blocking until an optimized footprint is found or the attack stops. The fine-tuning process handles the following conditions:
-
Positive Result Found
If the attack traffic is reduced after using the new footprints, the blocking module will continue to use this footprints. In addition, it will try to search for a more specific footprint by adding more footprints characteristics; this makes the footprint more specific and reduces false positive. -
Negative Result Found
If the newly applied footprint cannot reduce the attack traffic, it will look for other footprints. -
Attack Stop
If the attack stops, the IPS will stop applying the footprints immediately.
The main advantage of the behavioral DoS Attack protection is the ability to detect statistical traffic anomalies and automatically create an accurate attack footprint based on the traffic analysis. With the adaptive feed back mechanism to fine tune the footprint, this ensures the DoS protection with very low false positive.
c. Multiple Segments IPS – Virtual IPS
Our IPS is a high port density device. There is a total of 20 gigabit ports and it allows 9 independent network segments to be connected to it. Our IPS acts as multiple virtual IPSes which protects multiple LAN segments concurrently. The following figure shows the possible deployment of the IPS.
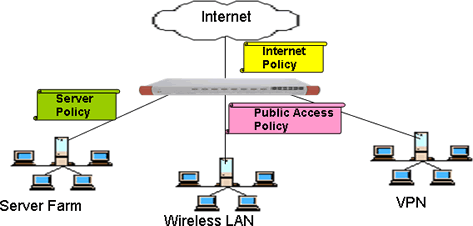
The advantages of the multi-segments IPS are as follows:
-
Low Cost; No need to buy multiple IPS for different segments
-
Centralize Administration of Policy
-
Maximize the Internal Network Protection
Attack can be stopped at the segment with IPS protected. It blocks the virus spreading quicker
d. Brute Force Protection for Central Servers and Application Servers
One of the main objectives of our IPS is to protect CityU’s central servers and applications. The following IPS features provide protection for the latter:
-
Server resources protection.
The following IPS modules protect against server resources-
SYN packet protection module
-
Connection Limit module
-
Bandwidth Management module
-
-
Application protection
The following type of attacks are protected by the IPS using signature-based protection-
Brute Force Password Guess
-
Buffer Overflow
-
SQL Injection
-
Cross-site scripting
-
e. Programmable API for Dynamic Policy management
One of the advantages of our IPS is the support of programming API that allows user to update the IPS policy dynamically. For example, if the mail server detects that some hosts are sending spam mail to the Internet, the administrator can make use of the programmable API to update the IPS policy automatically to block the Internet access of the host. Without such integration, it may take longer time to block the attack.
This greatly improves the interoperability and response time between different security systems. In addition, it integrates all the security devices into a single autonomy system.
Conclusion
Nowadays, tremendous numbers of software vulnerability are found everyday. In addition, the techniques used by the viruses/worms are evolving quickly; we must make use of the latest techniques to stop these attacks. The use of advanced features of our new IPS discussed above further tightens the security level at our Internet gateway. Besides, the vendor is working closely with us to incorporate new features into our IPS. This makes the CSC capable of responding quickly and directly to stop new attacks and provide maximum security protection for CityU.