Network Forensics: Finding a hidden needle in the haystack
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */
Network forensics is the technique in capturing, storing, and analysing network logs in incident events. It also comes in other names, such as specific packet mining, packet forensics, or digital forensics. Regardless of names, the idea behind is the same: to record every packet of network traffic (emails, database queries, Web browsing – all kinds of traffic traversing an organization’s network) into a single searchable repository to facilitate the detailed network examination. This paper presents challenges raised and technics to perform network forensics.
Introduction
Network Forensics gathers network activity evidences to address security breach and operational issues. Referring to SANS Institute notes, “Network forensics can reveal who communicated with whom, when, how, and how often. It can uncover the low-level addresses of the systems communicating, which forensics investigators will use to trace the pattern of conversation back to a physical device. The entire contents of emails, IM conversations, Web surfing activities and file transfers can be recovered and reconstructed to reveal the original transaction. More significantly, the protocol data that surrounded each conversation is extremely valuable.”1
In general, network forensics is best known as a methodology for investigating security incidents, such as data breaches and fraud cases. In securitytriggered event, an Intrusion Detection System (IDS) will raise an alert about suspicious network activity and security analysts will proceed to confirm the presence of an attack2. Therefore, the examination of a comprehensive record of network traffic will start as soon as the alert is raised. This facilitates the search and gathering of proofs for security experts during an incident breach. If the investigation result is positive, the next step will be the attack remediation. Without an ongoing packet analysis of network traffic, security analysts would have no hint whether a threatening activity occurred while the alert was raised.
|
Advanced Persistent Threat
Most cyber offences aim at disrupting systems, whereas APT attacks exploit vulnerabilities to collect sensitive data.
Therefore, the attacker will remain in the system as long as he can, in order to gather as data as possible. Main targets are governments or organisations with high-value information in sector such as defence or financial industries. The maintenance of access is paramount.
Main APT attacks are performed by groups. Some well-known threat groups have even been renamed as APT18 or APT28.
Social Engineering Case8
A manufacturing firm ranked among Fortune 500 companies was targeted by an APT. Four executives received an email containing a link. One of them clicked on it. Due to this action, the attacker was able to gather highly sensitive data stored in the victim’s computer and emails. Moreover, the company was performing Merge and acquisition. Due to this data leakage, the acquisition failed.
Social engineering does not required to be technical. Therefore, no-one is immune to the possible attack of APT.
|
Emerging Threat
Over the past few years, the emerging trend in Cyber Threats shows that actors behind Advanced Persistent Threat (APT) have become more and more well-coordinated. Moreover, APT attackers use wide range of exploits tools which were previously deployed by other types of cyber criminals. Therefore, discerning attackers’ goal becomes critical to evaluate incidents impact. Forensics experts will have to carry out the required verifications to determine it. Attackers will use the following tools to perform their APT:

Social engineering is a method generally used in cyber espionage mission. The “espionage actor” will create social media profiles and contact company employees in order to enforce them to download Backdoors.

APT creators are well-known in creating their own custom tools. Once, cyber criminals deployed more than 70 malware and utilised crafted malware to target the victim’s environment. Moreover, APT28,3 a Russia-based APT group, has systematically evolved its malware for more than seven years, creating malware platforms which give them flexibility in staying in a vulnerable eco-systems.


Maintaining persistent5 communication has always been a hallmark of APT / cybercriminals, who work to stay in an ecosystem until they’ve completed their mission. For instance, cyber criminals maintain subtle persistence by using wellknown vulnerable Windows start-up registry locations to launch their malware. This method had proved to be useful in remaining in the registry for more than five years.

Data theft usually happens on a broader scale, and it goes broader in its selected target of sensitive data subsets. Cybercriminals continue to steal personal identification information (PII) for other illegal purposes, such as fraud or even selling it in underground markets. Cyber-criminals even use PII to launch zero-day attack to gain money. Underground APT groups, such as APT186, , have been identified as the attacker behind the leak of US health data for Chinese drug company.7
Challenges
Several challenges need to be addressed in order to increase network forensics efficiency and subsequently provide opportunities for industry and academia to capture new competencies, capacities and finally better address network analysis issues. Generally speaking, there are four thematic challenges which stand out from others according to various case studies:

Large amounts of data set are transmitted through the network, in capacity of gigabytes a day. Therefore, it is tedious to look for evidences and it is almost impossible to find them. Consequently, this domain remains challenging and researchers have to focus on it.

Each packet header transmitted through network layer will have their source and destination stored in IP packet format. It includes MAC addresses, IP addresses, encapsulations and data, which can be potentially spoofed. Therefore, technical skills and use of reliable products purposebuilt are required to perform forensic analysis. Such products enable cases resolution through the analysis of network activity.

Forensic assessment can be executed through forensic software via collection, normalising, filtering, labelling, stream reassembly, correlation and analysis of multiple sources of traffic data. Although some sophisticated forensic tools already aimed at each of these tasks, the introduction of new features is blurring the distinction between categories. As a result, the number of suspicious behaviours over the network grows significantly. Therefore, only appropriate network activity data should be collected. Digital evidence should include raw network packets, which contain traffic details, logs data available from applications, authentication systems, routers and firewalls.

TCP reassembly9 is the collection of raw network traffic from a single source in order to present all data within a connection session as a complete stream. TCP reassembly is performed by protocol analysis tools, which isolate the specific communications taking place between two or more of the apparent endpoints or relay points. This is the first step in determining who communicated, when and what was transmitted. Most forensic tools provide a tree-oriented view of sessions and protocols used within the sessions. This comes with visual presentation of network traffic mapping which helps forensic investigators to understand exactly what happened on the network.
Requirements for Network Forensic
To facilitate investigations, network forensics generally will focus on three essential capabilities: capturing and recording data, discovering data, and analysing data.



Practical Approach in Network Forensics
In case of a security incident, an organisation will quickly engage forensic experts from Cyber Incident Response Team (CIRT). They will have to perform within two days investigation, consultancy and installation of forensic equipment to the client site, in order to establish the extent of the incident, and contain it within the 48 hours11. Below are the steps of a practical approach in Network Forensics.
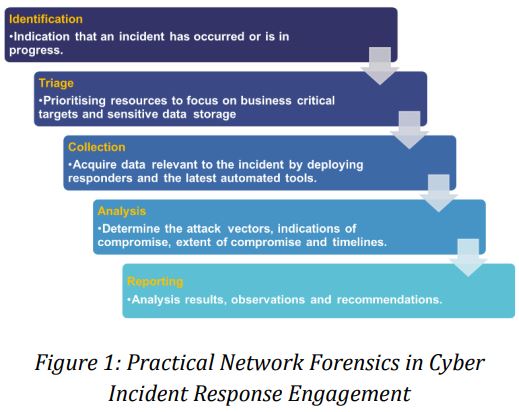
Identification: Indication that an incident has occurred or is in progress. This is the first step to identify the severity level of an incident and the entry stage of a CIRT engagement.
Triage: Prioritise resources and target segment to focus on business critical targets and sensitive data storages which have been compromised.
Collection: Acquire data and network behaviour related to the incident by deploying responders and the latest forensic tools.
Analysis: Determine the attack vectors, indications of compromise, extent of compromise and timelines of the incident.
Reporting: Provide results analysis, observations and remediation steps to close the incident.
Such is a standard practice in a 48-hour engagement; it is considered as the best approach to perform network forensic assessment. Evidences found within the two-day engagement provide arguments to the senior management for implementing further preventive measures.
Applications of Network Forensics
Applications of network forensics are not limited to PCAP, Wireshark or XYR, they can also find, explore and perform deep technical analysis of a cyber incident or network and system disruption when third party analyst tools fail. For examples:





Practical approach in dealing Zero-Day attacks requires network forensic tools and devices which are able to perform retrospective analysis of packets. This helps forensic investigators to identify if network has been compromised in the past and how the threats can be contained in future.
Use Case of using Network Forensics in a Universiti Teknologi Malaysia – AIS Environment13
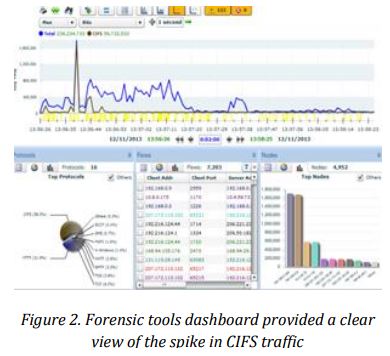
UTM-AIS run case study at their Cyber Forensic Lab in Malaysia to simulate cyber incident and study the effectiveness of their cyber incident response procedure on the campus, During the simulation process, the network based IDS on an enterprise network raised an alert about unusual activity on a server. (In the screenshots below, the compromised node is identified as the address 10.4.3.248). When a team of forensics analyst was conducting an investigation, they discovered that the server was compromised by a security attack. Unfortunately, the IDS logs provided no further information about the attack, as the list of other compromised systems or attacker’s details. With the aid of forensic tools – dashboard (in this case, WildPackets Compass), forensics experts were able to identify compromised system. In fact, the Common Internet File System (CIFS) traffic spiked shortly after the attack had begun. The screenshot on the left shows an example of such a CIFS spike.
One of the advantages about network forensic appliance in this scenario is that it recorded all network traffic around the time of spike; this gave the forensics experts an upper hand to examine network activity in depth and explore this burst of traffic and its consequences. To present the discovery process more accurately, the forensic analyst would start a Peer Map which showed all IP communications during the spike period. As suspected, the Peer Map revealed how the compromised server had communicated with several other internal systems.
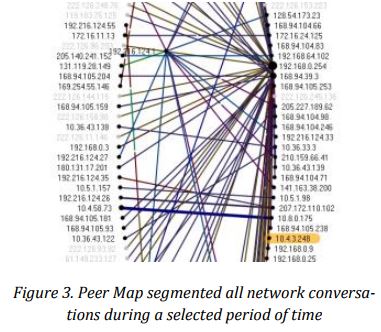
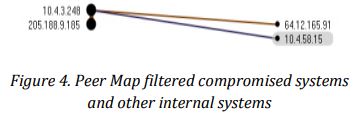
Afterwards, forensics analysts segmented detailed information on four internal systems during the critical time of CIFS spike. This would give forensic analysts the advantage of narrowing down the investigation scope, and enable them to conclude on the root cause, and how the communication with other internal systems occurred.
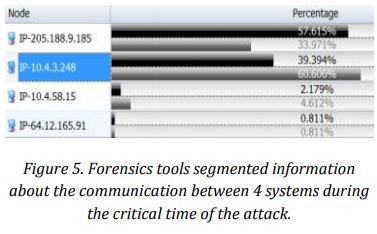
Eventually, forensic analysts were able to identify which servers they would have to focus on in order to contain the attack and reverse its effects. In addition to quarantining and repairing 10.4.3.128, the forensic team would also focus on 10.4.58.15, 64.12.165.91, and 205.188.9.185.
Benefits of Network Forensics
Counting on the robust network forensic methodology described above, university can react and response with the appropriate plan and countermeasures in case of cyber incidents. Suspicious network activity or intrusion activity can be picked up in time for a timely response. Crucial nodes or segments within all types of systems, from network devices to computers, can be further finetuned in specific areas of concern such as database, email, and log information. In today’s emerging cyber attacks14, a number of sophisticated attacks are programmed to erase log files, hiding the damage inflicted. In many of these cases, network forensic is the only way to uncover what happened. The benefits that can be reaped are evident and presented in very precise and accurate manners, such as environment recovery, forecasting, auditing, damage assessment, and beyond. With a variety of options in the network forensics triage, there can be many ways to explore what benefits each system can bring to the university infrastructure.
Conclusion
Network forensics is the technique of capturing, storing, and analysing network logs in security incident requiring highly professional skills. Forensic experts in CIRT team handle the investigation with sophisticated forensic method and tools in order to keep pace with today’s high-speed networks. New tools and forensic practices are mandatory to ensure that the IT unit of all universities keeps networks and systems stable and secure.
Starting from a vague security alert, forensic experts will make use of forensic tools to identify specific systems to quarantine and where to focus on during the clean-up of the attack. Network forensics enables the team to find evidences of the attack and trace its effects.
By investing in network forensics with the best practices listed in this paper, University IT Team can ensure that speed, availability and integrity of connectivity does not come at the expense of visibility, control, or security. User data privacy, security standards and reputation of the university will be fully protected and upheld.
References
- “Security 558: Network Forensics Course Description” 15 October 2015, Web, October 2015
- “Honey Pot Intrusion Detection System” K. L. Ogweno et al. 2014k pdf.
- “APT28, a window into Russia’s Cyber Espionage Operations?” APT, 2014, pdf.
- “Crimeware or APT Malware: Fifty Shades of Grey “ N. Villeneuve, 2014, pdf.
- “Advanced Persistent Threats – Attack and Defense” 2013 Web. October 2015, pdf.
- “The Chinese government has a clear motive to steal U.S. health data” Mark Sullivan Venture Beat News, 2014, pdf.
- “APT Gang Branches Out to Medical Espionage in Community Health Breach” M. Mimoso, 2014, pdf.
- “Gaining awareness to prevent social engineering techniques, attacks” May 2011, Web, October 2015
- “TCP Reassembly” 2015 Web. October 2015
- “A Comprehensive Review on Adaptability of Network Forensics Frameworks for Mobile Cloud Computing” S. Khan et
al, 2014, pdf. - “Good Practice Guide for Incident Management” ENISA, 2010, pdf.
- “Network forensic system for port scanning attack" Kaushik et al. 2010, pdf.
- “Tracing Source of Compromise Server” UTM Forensics Simulation Lab Assessment, 2013, pdf.
- “Security Threat Report 2014, Smarter, Shadier, Stealthier Malware” SophosLab, 2014, pdf.