Man-in-the-Middle Attack: Security and Privacy Concerns
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */
More and more transactions are performed online. Thus, a secured connection has to be ensured between the server and the client. However, connection mainly requires just a server authentication. The client identity is not checked, which allows attacker to intercept the communication and impersonate the user. This kind of attack is a Man-in-the Middle attack. This name is derived from basketball in which a player tries to intercept the ball that is exchanged between two other players.
Man-in-the-Middle Attack Progress
A Man-in-the-Middle (MIM) attack is an attack in which the attacker intercepts information exchanged between two persons. The two legitimate parties think they are communicating directly with each other and do not suspect the presence of the intruder.
There are two major forms of Man-in-the-Middle attack: eavesdropping and manipulation1.
- Eavesdropping
An eavesdropper just listens to the data stream and records it to analyze. It is a kind of data leakage more than a direct attack.
- Manipulation
In the case of a manipulation, data have to be redirected to an intermediate machine to allow data modification and enable the attacker to forward them to the legitimate recipient.
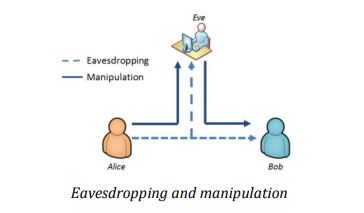
Man-in-the-Middle attack is a common threat during key exchange. For instance, Alice wants to send an encrypted message to Bob. Unfortunately, Mallory is monitoring the conversation. Alice will ask Bob his public key. Bob will sent his public key but Mallory will intercept it and send her public key instead of Bob’s one to Alice. Alice will encrypt her message with Mallory public key thinking it is Bob’s public key and send it to Bob. Mallory will intercept the message and decipher it thanks to her private key. Then she can modify it or just read it and send back to Bob the message encrypted with his public key. Bob will receive the message and think that it comes directly from Alice. He will be able to decipher it with his private key.

Once the attacker is established, he can just gathered information but he can also inject malicious code.
|
Difference between
Man-in-the-Middle
attack and sniffing2
A sniffer is a tool used by
hacker to capture and analyse
network packet. If
the network packets are
not encrypted, the data
can be directly read
thanks to the sniffer.
This attack is passive, the
attacker will just read the
packet and the traffic will
not be modified. Unlike
sniffing attack, Man-in-the-Middle
attack implies
an active third party. This
one can alter message
content and even inject
malicious code.
However, a Man-in-the-Middle
attacker is able to
sniff packet. It is the
eavesdropping form of the
MIM attack.
Great Cannon4
The Great Cannon is an attack tool that behaves as a Man-in-the-Middle attack. In fact, it will intercept web traffic and arbitrarily replace content. It is used to launch distributed denial-of-service attacks to disrupt websites operations.
The Great Cannon is able to inject traffic but also to directly suppress it. It does not sniffer all the traffic but only intercepts specific addresses.
As a complete Man-in-the-Middle attack, it can intercept unencrypted e-mail and alter its content without user’s detection.
In March 2015, Github has been attacked by the Great Cannon. Github characterized this attack as the largest DDoS attack of its history. This Man-in-the-Middle attack replaced a javascript file used for user tracking by another one which asked the user’s browser to indefinitely reload two pages at Github.
Bank threat8
In 2003, a group of hackers tried to attack several banks. Once was especially vulnerable and they succeeded in transferring $10 million within few hours.
The bank did not manage to localize them. Hackers decided to contact the bank president and offered two options. The first one was that the Bank would prosecute them but in this case, attackers would deny and notify the public on the bank’s poor security. The other one was to consider this attack as a security assessment requested by the bank that cost $5 million and hackers would return the other $5 million to the bank.
Finally, the president decided to give $5 million to the attacker as a security assessment.
|
Attack Techniques
The techniques used for Man-in-the– Middle attack can be classified according to the type of network environment3:

A local area network is a bounded area in which, computer are interconnected (eg. a university, an organization…). In this kind of network, communication between computers is easier because trusted connections are already implemented. Thus, specific techniques will be employed by the attacker.
ARP poisoning: the attacker sends falsified Address Resolution Protocol messages. Usually, the attacker associates his MAC address with the victim’s IP address. Thanks to that, the attacker retrieves any traffic sent to the legitimate IP address. Finally, the attacker can modify the packet.
DNS spoofing: the attacker sniffs DNS request and replies before the real DNS server. Traffic is diverted to the attacker’s computer.
IP address Spoofing: IP packets are created with a forged source IP address in order to impersonate another computer system. This attack is easier to set up in a local network where trust relationship is already implemented.
Port stealing: the attacker redirects traffic to another port of the Ethernet switch. To do it, the attacker floods the victim host’s switch with forged ARP packets. These packets have the victim host’s MAC address as source address and the attacker host’s MAC address as destination.

DHCP spoofing: the attacker replies before the DHCP server and diverts traffic. He can then manipulate the victim’s IP address, the gateway address assigned to the victim and the DNS address.

IRDP spoofing: the attacker will remotely add new route that will be preferred over the default one from the DHCP. The host will follow the attacker’s route instead of the legitimate one.

Remote access is less lenient because computers are not interconnected.
DNS poisoning: the attacker can brute force the DNS by replying before the real DNS and trying to guess the correct ID. Otherwise, the attacker can send a dynamic update to the victim DNS. As soon as the DNS processes it, the attacker gains control.
Traffic tunnelling: The attacker will collect sensitive information exchange between two persons thanks to traceroute, port scanning or photo scanning.
Detection Techniques
A Man-in-the-Middle attack is generally hard to detect. However, some techniques enable detection of malicious behavior. Wireless sensor networks can detect MIM attack in a timely fashion. Moreover, attackers can always do mistakes. Users have to remain alert. In case of suspicion, network forensics can be handled on the server IP address, the server DNS name and the X.509 certificate of the server.

Wireless sensor networks can be used to detect MIM attack5. In fact, they can estimate distances thanks to distancebouncing protocols. The distance is estimated based on precise timing. If the time to receive a message is more important than a certain delay, the message will be rejected.

Third party program can be used to detect an intruder. Intrusion detection system as Snort will monitor the network traffic of hosts. This technique is only feasible for single host monitoring but will not be relevant for an entire network.

In a wired network with wireless access point, attackers can use the Wi-Fi in order to intercept information. Several techniques can help to detect wireless from wired network thanks to the difference of capacity and variability characteristics between both kinds of networks6.
Client-side bottleneck bandwidth can be used to determine the inter-arrival between two packets. The value will help to determine the nature of the network (wired or wireless).
Round Trip Time (RTT) can be used to detect rogue access point. RTT corresponds to the time required for a signal to go from a source to a destination and to come back. This technique can help to separate wired from wireless access. This technique can present false positive and thus classified a legitimate user as an attacker.
Radius authentication server can authenticate devices and thus also detect rogue access point. It will only detect rogue access point coming from an Internet Service Provider which has a radius authentication server installed.

References and certificates send by the server should be compared and connection should be established only in case of perfect matching7.
Certificate fingerprint can also be compared against a reference value. The certificate fingerprint is a public key encrypted with cryptographic hash function such as sha-1 or sha-2.
Checking certificate can help to detect MIM. In fact, certificate should be signed by a trusted certificate authority. Users should mistrust certificates that have been revoked or recently changed as well as certificates used on several websites.
In case of system or browser warning about certificate validity, user should not continue his request.


A user can detect that the HTTPS indication is missing in the browser. In fact, when client connect to a secure website as bank account, the page should be encrypted but sometimes, https is not indicated in the browser. That means that the connection should not be trusted. A Man-in-theMiddle attack should be occurring.
Defense Techniques

In a MIM attack, the attacker can intercept the legitimate certificate sent by a website to a client and replace it by another one. The client will accept it and thus, will have accepted an untrusted certificate. A solution to prevent it is to automate certificate assessment. In fact, MIDAS (Man-in-theMiddle Distributed Assessment System), will validate certificates through a given network. The mechanism consists in classifying certificates as trusted or untrusted, according to information gathered from different sources.

DNSsec (Domain Name System Security Extensions) is an alternative to DNS9. It ensures the validity of data received and authenticity of the DNS records. Public key cryptography is used to do it.
It is still at an early stage in its deployment.

In the case of a one-way authentication, only one party is ensured of the other one identity10. Thus, the conversation can be eavesdropped between the non-authenticate party and the certified one.
For instance, if a client log into a bank websites, only the bank’s server provides a certificate. Thus, requests made by the client to the server can be intercepted. Mutual authentication will defeat this attack. No one will be able to impersonate the client identity anymore.

SSL creates and establishes a secure communication between devices and prevents eavesdropping. However, a bad implementation could lead to the opposite result. Parties have to validate that the remote connected party is legitimate. Then, they create a key to encrypt data exchanged between them during the session.

Consequently, SSL can be compromised whether the key has been stolen. In this case, there is no way for the user to know that the server is not trustworthy anymore. The client can also trust a CA whose root key has been stolen.

In case of a Man-in-the-Middle attack, the server will not notice any issues; however, some protections can be done from the client side.
Firstly, he should ensure that secured connections use HTTPS. Secondly, the likelihood of traffic interception is lower on the home network than on the work network. In fact, at home only a small number of computers are related and they all belong to the same family whereas, at work, the potential sources of attacks are multiplied. Thus sensitive websites as online banking should be accessed from home.
Finally, these kinds of attacks are mainly executed from inside the network, thus, internal machines have to be well-protected12.
Conclusion
Man-in-the-middle attacks remain hard to detect. More and more cryptographic protocols include endpoint authentication in order to prevent Manin-the-Middle attack. However, whether users used untrusted websites these preventions will remain useless. A wise use of the Internet can limit the risk and improve the time of attack detection.
References
- “Man-in-the-Middle attack” August 2015 Web. 6 August 2015
- “What is the difference between Man-in-the-Middle attack and sniffing” August 2014 Web. 10 August 2015
- “Network security: Man-in-the-Middle attack techniques” December 2013 Web. 3 August 2015
- “China’s Great Cannon” April 2015 Web. 10 August 2015
- “Detecting and Defeating Advanced Man-in-the-Middle Attacks against TLS” by E. de la Hoz et al. 2014 pdf
- “Man-in-the-Middle Attacks Detection Scheme on Smartphone using 3G network” by J. Lee et al. 2012 pdf
- “Man-in-the-Middle? – No, thank you!” June 2013 Web. 6 August 2013
- “Unauthorized Access: Security Breach Example” October 2011 Web. 7 August
- 2015
- “DNSsec an introduction” October 2014 Web. 7 August 2015
- “Can mutual authentication beat phishing or Man-in-the-Middle attacks” August 2015 Web. 7 August 2015
- “SSL handshake with two ways authentication with certificates” August 2008 Web. 10 August 2015
- “Understanding Man-in-the-Middle attacks” June 2010 Web. 6 August 2015