Wireless Security: Technical Point-of-View
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */
Wireless network (Wi-Fi) is now widely established and utilized at home, offices and everywhere in public areas such as rail stations, streets, and etc. This newsletter provides the technical knowledge of Wi-Fi technologies, relevant threats and countermeasures for building a secure internal Wi-Fi network.
Wireless Technologies
Classification of Networks
Technological advancement in wireless communications has led to the worldwide proliferation of networks. The various kinds of network technologies developed can be classified into the following categories according to their range of coverage:
Wireless Wide Area Network (WWAN)
WWAN offers the largest coverage. Voice and data can be transferred between mobile phones via messaging apps, web pages and video conferencing. In order to secure the transfer, encryption and authentication methods are adopted. Examples of WWAN are 4G, 3G and 2G networks.
Wireless Metropolitan Area Network (WMAN)
MAN (Metropolitan Area Network) covers across the entire city and WMAN provides the Wi-Fi network similar to MAN. WiMAX and Wireless MAN are both examples of this kind.
Wireless Local Area Network (WLAN)
WLAN is an 802.11i wireless network that facilitates the access of corporate environment. It is optimal for low range access with high bandwidth requirements. Internal Wi-Fi within the office area can be regarded as WLAN.
Wireless Personal Area Network (WPAN)
WPAN has the least coverage among all. It is usually adopted for devices which perform Bluetooth or Near Field Communication (NFC) functions. In Hong Kong, NFC-enabled devices like Octopus Card, is commonly used as a convenient form of electronic payment for public transport, retail shops and other services. In Hong Kong, most banks issue credit cards with a small chip implant to improve the payment processing time and its security level.

The following introduces the technologies and characteristics of wireless network.
WEP
Wired Equivalent Privacy (WEP)1 is a wireless security algorithm introduced as part of the 802.11 standard in September 1999. It used the recognizable key of 10 or 26 hexadecimal digits, and frequently used in router configuration.
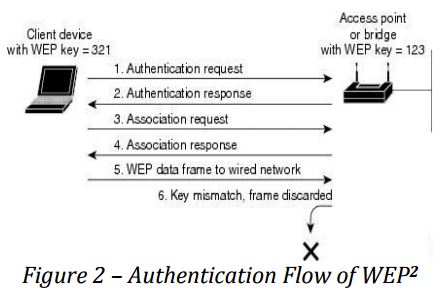
Illustration above shows the flow of WEP authentication. If a non-root bridge tries to access the client device without authorization, the WEP will automatically reject the connection.
WEP encryption uses RC4 as a stream cipher, this serves the purpose of “IV” which is transmitted as plain text to avoid any repetition. However, a 24-bit IV is not long enough to ensure nonrepetition – there is still a 50% chance that the same IV will appear after 5,000 packets2.
Meanwhile, tools such as Aircrack, AirSnort, WEPCrack and DWEPutils which can be easily obtained from the Internet are capable of cracking WEP key in less than a minute. Indeed, there is a serious security weakness of RC4 adoption.
In summary, it is insecure to use WEP to access wireless network3.
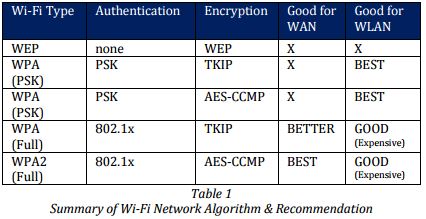
WPA & WPA2

|
New Spear Phishing Attack Bypasses Two Factor Authentication5
By clicking on the “forgot password” link and requesting the verification code, the attacker prompts the email provider to send an SMS message with the code to the victim’s mobile phone.
To get the code, the attacker then sends the victim a separate SMS message saying something like, “Google has detected unusual activity on your account. Please respond with the code sent to your mobile device to stop unauthorized activity.”
The victim replies with the code, and the attacker gains access to the victim’s email account.
As Grzonkowski notes, after resetting the account password, the attacker could send the victim an SMS stating, “Thank you for verifying your Google account. Your temporary password is [TEMPORARY PASSWORD.”
Wi-Fi Freeloading: Now a Crime in U.K.7
A British man has been fined and given a suspended prison sentence for connecting to a stranger’s WiFi access point without permission, according to a BBC story. There is no indication that he did anything improper while connected; all he did was to park his car in front of a stranger’s house and connect his laptop to the stranger’s open WiFi network. He was convicted of “dishonestly obtaining an electronic communications service”.
Wireless network vulnerability assessment checklist8
1 – Discover Nearby Wireless Devices
2 – Investigate Rogue Devices 3 – Test Owned Access Points 4 – Test Owned Stations
5 – Test Owned WLAN Infrastructure
6 – Apply Test Results
Still having no idea for how to perform the assessment? Check with the security consultants for more advisory and service.
TJX Hacker Gets 20 Years in Prison9
Hacker Albert Gonzalez was sentenced to 20 years in prison in 2010 for leading a gang of cyber thieves who stole more than 90 million credit and debit card numbers from TJX and other retailers.
The string of hacks began in 2005 when Gonzalez and accomplices conducted war-driving expeditions along a Miami highway and other locations in search of poorly protected wireless networks, and found easy access into several retailer networks.
Hacked the public Wi-Fi in 11 minutes by 7- year-old child12
Just two days after an investigation had revealed how much personal information public Wi-Fi networks could ‘suck’ from phones, a child showed how easy the hotspots are to hack.
A seven-year-old broke into a Wi-Fi hotspot in just 10 minutes and 54 seconds after watching an online video tutorial.
The ethical hacking demo was carried out under the supervision of an online security expert to highlight just how vulnerable the networks are.
Security and QoS Unite15
Until recently, quality-ofservice and network security technologies lived in separate worlds. But they have something important in common. Certain types of attacks on network security affect application performance -- and ensuring application performance is the main mission of QoS.
By Joanie Wexler
Wardriving Burglars Hacked Business Wi-Fi Networks16
Three men were indicted last week by a federal grand jury for hacking at least 13 Seattle-area businesses' wireless networks to steal sensitive information, as well as burglarizing the premises of at least 41 businesses.
One of the affected businesses was Concur Technologies. According to a breach notification sent to the New Hampshire Attorney General's Office in December 2010, a November 2010 break-in to the premises of the business resulted in the theft of computer equipment containing unencrypted data on 1,017 employees, including their names, addresses, dates of birth, and social security numbers.
"Any company worth its salt should have realized that using WEP is about as much use to secure you as cotton or wool. It's not going stop anything," said Graham Cluley, senior technology consultant at Sophos, in an interview. "With PCI, for instance, they said that companies should stop using WEP, years ago. You need more sensible, hardened encryption, if you're going to have wireless communications."
|
Wireless Threats
Despite the benefits brought by wireless network technology, its derivative potential threats towards the network security should not be underestimated.
Different types of attack outlined in the following paragraphs and tables (Hacker methodologies and tools6) can be categorised as Active Attack and Passive Attack. The former includes DoS, Masquerade, Replay and Message Modification while the latter one includes Eavesdropping and Traffic Analysis.
Authentication Attacks
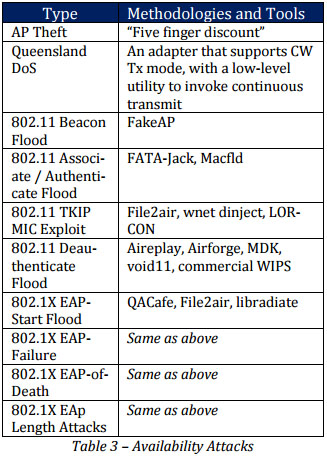
The main objective of Authentication Attacks is to steal the user’s identification and credentials for the sake of accessing the private network and its services. A list of types, methodologies and tools is captured in Table 2 for a quick reference.
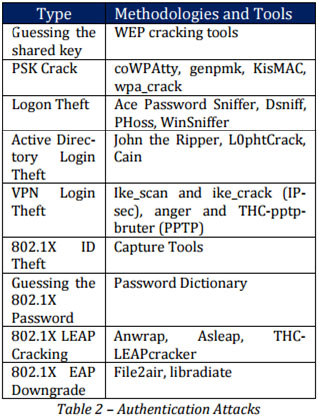
Availability Attacks
Denying wireless services access to legitimate users can result in Availability Attack.
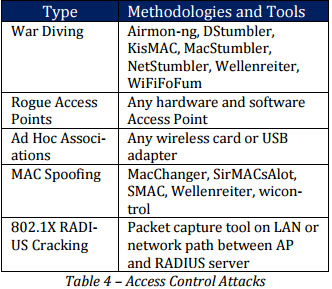
Access Control Attacks
Bypass wireless access control measures like AP MAC filter and 802.1X port access control is the main objective of Access Control Attack.
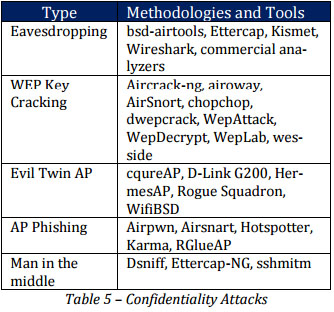
Confidentiality Attacks
Attacks that attempt to intercept sensitive information sent over wireless network, whether in the clear text, encrypted by 802.11 or higher layer protocols, is called Confidentiality Attacks.
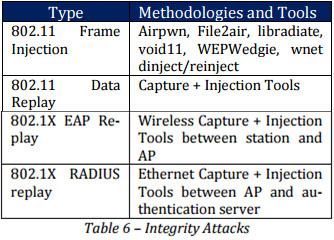
Integrity Attacks
By adopting Integrity Attacks, fake information or data is sent to mislead recipient for the purpose of financial theft.
Dip Deeper into Attacks
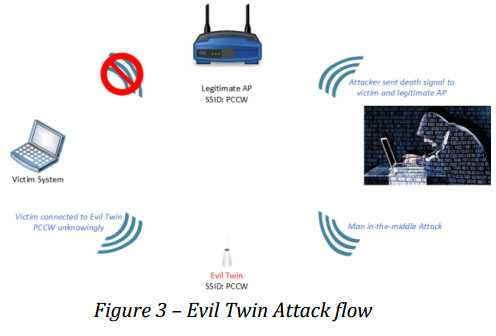
Here are the illustrations that explain the three common attacks at Wi-Fi network: Evil Twin Attacks, Wireless Sniffing and Peer-to-Peer Connection.
Evil Twin Attacks – Hackers disguised as legitimate user employ rogue Wi-Fi access point (AP) to eavesdrop communications. The process is similar to that of Phishing Scam (Figure 3). The steps to create an Evil Twin Access Point10 easily available from the Internet.
Wireless Sniffing – Unlike Evil Twin, attacker does not need to set up the rogue AP but simply deploy a sniffer tool to intercept data transmission via Wi-Fi network (Figure 4). It is difficult for victim to detect such attack unless network monitoring tool is deployed.

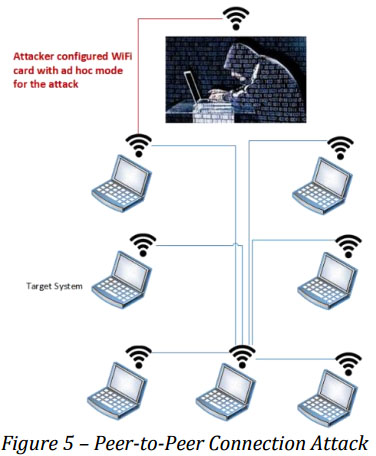
Peer-to-Peer Connection Attack – When all laptops configure wireless cards as ad-hoc mode and are connected together to form a network, attacker can connect to this network by adopting the same configuration, and consequently gain access to sensitive data (Figure 5).
Internal Wi-Fi Infrastructure
Security Best Practices to Implement an Internal Wi-Fi Infrastructure
After learning the possible security threats of Wi-Fi, the following security measures are highly recommended for the planning, implementation and operation of an internal Wi-Fi within a University environment:
Network WIPS Deployment – Deployment of Wireless Intrusion Prevention System (WIPS)11 can monitor radio spectrum for any existing unauthorized AP activities such as AP redirection, significant signal strength changes, AP spoofing and soft APs. When suspected AP activities are identified, alert will be generated and logged. Meanwhile, the high-risk connection will be disabled immediately and automatically.
To facilitate the deployment of WIPS, three approaches can be considered depending on budget and scale.
The first approach involves the installation of the lower-end AP which performs two roles: provide Wi-Fi connectivity and simultaneously do periodic scan for rogue APs. However, it is not very effective.
The second approach which is known as integrated WIPS, requires installing the sensor together with the AP for rogue AP scanning and seems to be more effective.
The final approach is called WIPS overlay, it can be implemented by the installation of sensors throughout the whole building; scanning result will be forwarded to the centralized Wi-Fi management server for further analysis, action and log archiving purposes. This approach is the most expensive one among the three as hardware implementation is required, but it is also the most effective one13.
Access Control Attack and Confidentiality Attack can be addressed by implementing such solution.
Wireless Bandwidth Management – The best way for individual user with comparatively low risk to seek higher security protection is to use Quality of Service (QoS)14 technique. QoS covers the aspects of network bandwidth, latency, jitter and reliability.
One of the key functions of QoS is inserting control over demanding bandwidth usage like BitTorrent, online games, HD movies or else. For business sector, QoS helps to control access right and balance usage, internal applications, videos streaming, VoIP calls and etc.
Previous Wi-Fi routers carried traditional QoS; however, this required strong technical knowledge and experience to configure the settings. Now the latest router models provide a user-friendly way of implementing QoS: Intelligent QoS. It helps to prioritize the bandwidth in four categories such as voice, video, applications and background activities (internal printing jobs, file downloads and other traffic).
Implementation of QoS together with traditional IDS/IPS system enhances the level of network security, prevents attack from unexpected and suspicious behaviours which is bandwidth demanding.
Implementing wireless bandwidth management can prevent Availability Attack.
Network Segregation – Not only can Network segregation minimise the risk of sensitive data leakage and unauthorized access of the network, it can also reduce the possibility of single point of failure when the network is comprised.
For secure internal Wi-Fi planning and implementation, the following tips are worth considering:
Multi-level Network Controls – The more layers of network segments are added, the more difficult for cybercriminals to tap into the network. If the existing network infrastructure restricts such change, consider implementing isolation for the newly built internal Wi-Fi or networks that planned to be built, and revamp the whole infrastructure by phases if necessary.
Whitelist or Hybrid Approach – Instead of blocking or allowing certain types of network access, define both whitelist or blacklist respectively for acceptable or unacceptable traffic that are already known. Continuous audit and review of these listing should be performed annually or by ad hoc.
Least Privileged Access Control – Even though service vendors request to access the network (including Wi-Fi) for maintenance or project-wise tasks, the mandatory access control should be in place and access log should be properly configured and securely stored for review for the sake of security incident investigation.
This security control can block Integrity Attack proactively and effectively.
Mandatory Access Control – Mechanism like MAC Addresses Registration of pre-approved university devices and self-registration of MAC Address from service vendors’ devices should be properly updated, defined and operated. Regular review and audit for MAC addresses access log should be performed to avoid rogue school devices MAC connection, an issue arising from “Bring Your Own Device (BYOD)”.
For guests’ devices, Guest Wi-Fi at DMZ can be configured separately at another VLAN for the purpose of Internet connection; MAC addresses control to deny any school devices connection to this Guest Wi-Fi has to be configured as well.
By adopting this security measure, Access Control Attack can be blocked effectively.
Network Encryption Technique – When using Wi-Fi network, strong encryption protocol should be adopted at all APs.
The latest Wi-Fi encryption protocol, WPA2 with AES mentioned earlier in this newsletter, is strong enough for network encryption, but regular technology review and update are certainly needed.
By applying this practice, Integrity and Access Control Attacks can be avoided.
Virtual Private Network (VPN) – Some overseas Universities provide free VPN connection for their staff and student to access the Intranet externally17. VPN service can secure data transmission and it is not complex to configure and use. University should consider applying this service if there are frequent academic activities held outside campus.
Conclusion
The landscape of IT security threat changes rapidly. It is prudent for University management and technical staff to keep abreast of the threats and implement controls to eventually cope with these challenges.
When planning, building and operating an internal Wi-Fi infrastructure, it is important to understand the risk implications and apply the security best practices as described in this newsletter. It is also the university’s responsibility to maintain the confidentiality, integrity and availability of information security.

References
1. “Wired Equivalent Privacy” Wikipedia, WEB, 19 June 2015
2. “Configuring Authentication Types” Cisco, WEB, 19 June 2015
3. “Attacks on the WEP protocol – Erik Tews, Page 81” 15 December 2007, PDF, 19 June 2015
4. “Wi-Fi Alliance Home Page” WEB, 19 June 2015
5. “New Spear Phishing Attack Bypasses Two Factor Authentication” 22 June 2015, WEB, 6 July 2015
6. “A list of wireless network attacks” WEB, 23 June 2015
7. “Freedom to Tinker” 1 AUG 2005. WEB, 23 June 2015
8. “A wireless network vulnerability assessment checklist – TechTarget” WEB, 23 June 2015
9. “TJX Hacker Gets 20 Years in Prison” 25 MAR 2010. WEB, 23 June 2015
10. “How To Create An Evil Twin Access Point (with WPA/WPA2 Capture) – YouTube” WEB, 23 June 2015
11. “Wireless intrusion prevention system – Wikipedia” WEB, 24 June 2015
12. “Hacking Wi-Fi is child’s play! 7-year-old shows how easy it is to break into a public network in less than 11 MINUTES – MailOnline” 21 JAN 2015 WEB, 24 June 2015
13. “Motorola AirDefense Services Platform” PDF, 3 July 2015
14. “What is QoS? – Microsoft” WEB, 24 June 2015
15. “Security and QoS Unite” 19 JAN 2014 WEB, 6 July 2015
16. “Wardriving Burglars Hacked Business Wi-Fi Networks” 23 SEPT 2011. WEB, 23 June 2015
17. “Accès vpnssl : Documentation” WEB, 6 July 2015