Main navigation
News
December 2012
by Manfred Chan
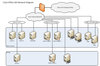
To exploit the cloud computing technologies, CityU has decided to adopt the Microsoft Office 365 (Office 365 hereafter) for Education. Office 365 is the cloud computing solution offered by the Microsoft for academic institutions. As an initial step, the Computing Services Centre (CSC) will replace ...
by Helium Hung

The CityU Search was powered by the public Google Search (a service hosted by Google) since 2005. After Google announced the availability of their enterprise solution for Asia-Pacific region in late 2009, the Google Search was replaced by the Google Search Appliance (a CityU locally hosted service) ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ In view of a numerous benefits of virtualisation, virtualisation technology has recently gained popularity in the marketplace. According to Gartner, percentage of workloads ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Virtualisation is the separation of resource or request for a service from the underlying physical delivery of the service. It can dramatically improve the efficiency and ...
by Joe Lee

In response to the University's emphasis on Discovery & Innovation and the subsequent implementation of Discovery-enriched Curriculum (DEC) in academic year 2012-13, the C hief I nformation O fficer together with the Department of Computer Science ( CS ) proposed to set up a few DEC Labs for ...
by Tony Chan
Taking a huge leap forward, Microsoft launched the latest version of the Windows Operation System – Windows 8. The new operating system radically changes the way Windows works by introducing a new shell and user interface designed to be used with touchscreens yet maintaining certain compatibility ...
September 2012
by Helium Hung
Introduction The central web hosting service is set up to provide a consolidated, fully monitored and managed environment for hosting departmental and project websites for all departments and offices. The hardware and software offered by the central web service are maintained and supported by the ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Code injection attacks pose massive threats to the IT environment within universities. They could allow hackers to compromise universities' network, access and destroy their data ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Code injection attacks typically occur when inputs has not been adequately validated before execution. The basic principle is to provide some form of input with additional ...
by Joe Lee
Microsoft officially launched its latest web browser Internet Explorer 9 (IE9) in mid-March 2011. In comparison with IE8 and IE7, IE9 is clearly faster and safer than its predecessors. Furthermore, Microsoft claims that IE9 even outperforms some rival browsers. In order to allow offices, support ...